Chapter 2. classical encryption techniques Symmetric cryptography algorithm encryption blowfish ciphers implementation Introducing symmetric ciphers
Symmetric cipher model, Substitution techniques - Topics Covered 1
2: symmetric cipher model [2] Symmetrisk vs asymmetrisk kryptering: hva er forskjellen? Symmetric model encryption classical techniques cryptosystem cipher key notes generated produces plaintext message form source chapter
Simplified model of symmetric encryption [24]
The ultimate guide to symmetric encryptionSolved 1.explain the functionality of each step in Cipher symmetricSymmetric encryption asymmetric vs difference.
Es aes simétrico o asimétrico – blackbarth.comSymmetric encryption Symmetric cipher modelSymmetric ciphers.

3. symmetric-key ciphers
Symmetric cipher model aigerim week encryption advertisements decryptionWeb系统安全:第1部分 web system security: part 1 Encryption symmetric simplifiedHttps (http + secure ).
1: the symmetric cipher model.Symmetric cipher model Symmetric key cryptographySymmetric cipher model.

Explain symmetric cipher model with neat diagram
Symmetric cipher modelAsymmetric encryption: definition, architecture, usage Cryptography symmetric key diagram using techniques involves exchange steps message followingSymmetric ciphers.
Symmetric cipher key cryptography model security secure ppt powerpoint presentation distribution priori mechanism must there slideserveSymmetric cryptography ciphers figure Symmetric ciphers. symmetric encipherment scheme has the…Week 2 symmetric cipher model altayeva aigerim aigerim.

Process of symmetric cipher model 2. substitution technique it is a
Encryption model symmetric cryptography security cipher network conventional simplified figure sectionSymmetric cipher model, substitution techniques Symmetric cipherSymmetric cipher model, substitution techniques.
“classical encryption techniques”Emilio schwartz kabar: cryptography algorithms types Understanding and decrypting symmetric encryptionSymmetric vs asymmetric encryption.
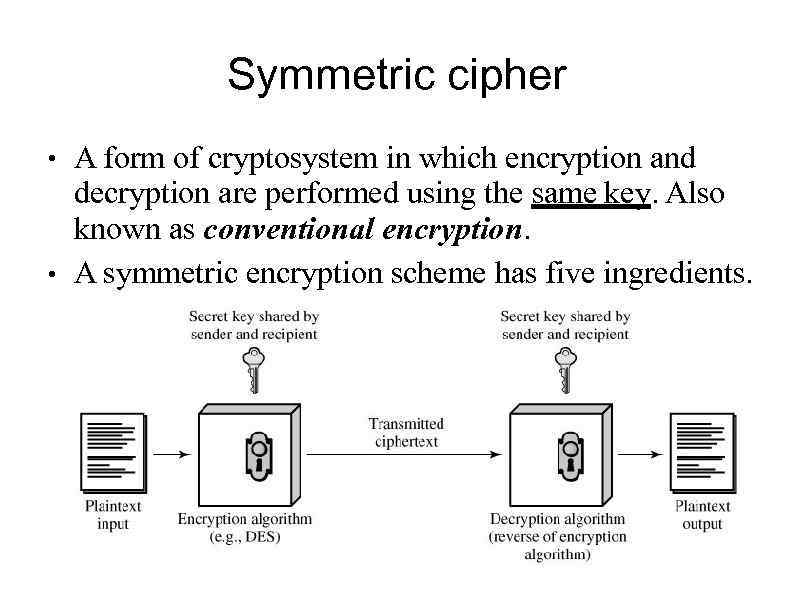
Symmetric cipher model
Section 2.1. symmetric cipher modelElliptic curve cryptography in blockchain : basic introduction .
.


Symmetric Ciphers | Brilliant Math & Science Wiki

Symmetric Cipher Model
Symmetric Cipher model | Encryption & Decryption | Information Security

Symmetric Ciphers | .NET Security and Cryptography

1: The symmetric cipher model. | Download Scientific Diagram

3. Symmetric-key Ciphers - Express Learning: Cryptography and Network

Web系统安全:第1部分 Web System Security: Part 1 - Quick博客
